Happy Monday, and welcome to CIO Upside.
Today: With cybersecurity budgets getting tighter, bug bounty programs may be enterprises’ best bet at spotting vulnerabilities without breaking the bank. Plus: Zoho’s Raju Vegesna discusses why the company built its own LLM; and IBM’s recent patent could improve data pipelines in real time.
Let’s jump in.
How Bug Bounty Programs Can Help Combat Ransomware Attacks

The U.S. is now the ransomware capital of the world.
Enterprises and organizations in the country are the targets of 50% of global ransomware attacks, according to a recent Zscaler ThreatLabz report, with manufacturing, technology and healthcare bearing the brunt. It gets worse: While ransomware attacks have climbed 146% in the past year, cybersecurity budget growth has shrunk to the lowest rate in five years.
In that ominous situation, it may take a hacker to stop a hacker. Enter bug bounty programs, or ethical hacking initiatives that allow researchers to find and report vulnerabilities before they can be exploited.
The most effective way to start is by combining a vulnerability disclosure program with a private bug bounty program, Crystal Hazen, senior bug bounty program manager at HackerOne, told CIO Upside.
A vulnerability disclosure program creates a “reactive net,” said Hazen, offering a “structured, always-on channel for any researcher to safely report vulnerabilities.” Meanwhile, a private bounty program invites a select group of vetted researchers to test your highest-priority assets, she added.
This dual-track approach enables organizations to scale operations in a controlled way by building coverage, fine-tuning internal triage and learning how to operationalize findings before going public, Hazen explained.
- The foundation of successful bug bounty programs includes a clear scope and clear rules of engagement for ethical hackers, fast and respectful communication with researchers, and tight coordination between security, engineering and legal teams, Hazen said.
- Through these dual programs, companies can access highly skilled global researchers and at far lower costs than conventional cybersecurity vendors.
- Ethical hackers know the ins and outs of the cybercriminal underworld, threat actors’ playbooks and techniques, and how they continually evolve their attacks. The ability to think like a hacker allows them to detect and patch vulnerabilities or bugs before a threat actor exploits them.
Embraced by companies from Apple to OpenAI along with a variety of big, medium, and small businesses in other industries, bug bounty programs have come a long way since their inception. And HackerOne is just one company that offers bug bounty services, with competitors including BugCrowd, YesWeHack, and Synack.
“While you can definitely hire a consultant to help you set up a (bug bounty) program, there are also entire companies dedicated to running a bug bounty program for you,” Tim Erlin, security strategist at Wallarm, told CIO Upside. “Setting one up from scratch by yourself isn’t necessary.”
These programs are customizable to your enterprise’s budgetary needs, allowing each company to adjust the price and scope. “Since organizations can set the bounties themselves, they have control over the economics to some degree,” said Erlin.
When pitching boards and executives for buy-in, CISOs and CIOs should present Return on Mitigation (RoM) bottom lines.
Though return on investment can be tricky to track in cybersecurity, measuring “return on mitigation,” or the value of preventing losses versus the cost of security efforts, can help provide context for the value these programs can bring, said Hazen.
HackerOne’s bug bounty program calculated a 700% return on mitigation, “meaning every dollar spent delivered $7 in estimated value,” Hazen said. “Traditional (return on investment) calculations fall short when measuring cybersecurity impact.”
“Bug bounties focus researchers on what matters most,” Hazen said.
Why Zoho Built its Own Proprietary Language Model
![In this photo illustration, the Zoho Corporation logo is seen displayed on a smartphone screen. (Photo by Thomas Fuller / SOPA Images/Sipa USA) *** Strictly for editorial news purposes only *** (Newscom TagID: sipaphotostwentytwo000199.jpg) [Photo via Newscom]](https://www.thedailyupside.com/wp-content/uploads/2025/08/sipaphotostwentytwo000199-scaled-1600x1067.jpg)
How much ownership do you want over your tech stack?
That’s the question that Raju Vegesna, global chief evangelist at cloud software firm Zoho, and his team pondered when deciding to build Zia, its own proprietary language model, from the ground up. Building Zia has allowed Zoho more control over the privacy, accuracy and outcomes of its AI deployments, said Vegesna.
“Most cloud companies don’t own their clouds,” said Vegesna. “And most AI companies don’t own the key part that makes them an AI company, which is the model, which is the heart of it … It’s like car companies that don’t make their engines.”
Zia isn’t just a single large language model, said Vegesna, but rather several language models of different sizes, patched together.
- Rather than using one massive model for every task, the system automatically routes tasks to the one that’s the best fit, depending on the complexity of the query. If it’s a simpler task, for example, it may be routed to the smaller Zia model that has 1.6 billion parameters. By early next year, the company aims to implement a 200 billion-parameter model into Zia.
- The adjustable framework allows Zoho to cut AI-related costs by only using the amount of compute necessary for any given task, said Vegesna.
- “There’s a role for everything,” said Vegesna. “And it comes down to the problem we are trying to solve. You don’t need an LLM for anything; that will require a bunch of resources.”
Along with lowered costs and energy efficiency, one of the biggest benefits of building an internal model is privacy, said Vegesna. By creating its own model from scratch, Zoho has been able to control the input and “guarantee the output in terms of privacy,” said Vegesna, especially because the company “doesn’t believe in training on customer data.”
Alternatively, in fine-tuning one of the major LLMs or building from an open source model, privacy and accuracy wouldn’t be as easy to guarantee to customers, said Vegesna. “We do not have much insight into what data it was trained on.”
“By not controlling the input, we cannot stand up to our word to our customers and say that we’re going to respect their privacy,” Vegesna said.
Though building these models isn’t a simple endeavour, enterprises interested in AI need to ask themselves whether technology sits at the core of their company, he said. If your products and services revolve around technology, or heavily rely on it, then the benefits may outweigh the costs.
“If technology excites you, I would say do it,” said Vegesna “If you’re a technology company, you’ve got to own the technology. If you’re a car company, you have to own the engine.”
IBM Patent May Help Clean Data Pipelines
Not all data is created equal.
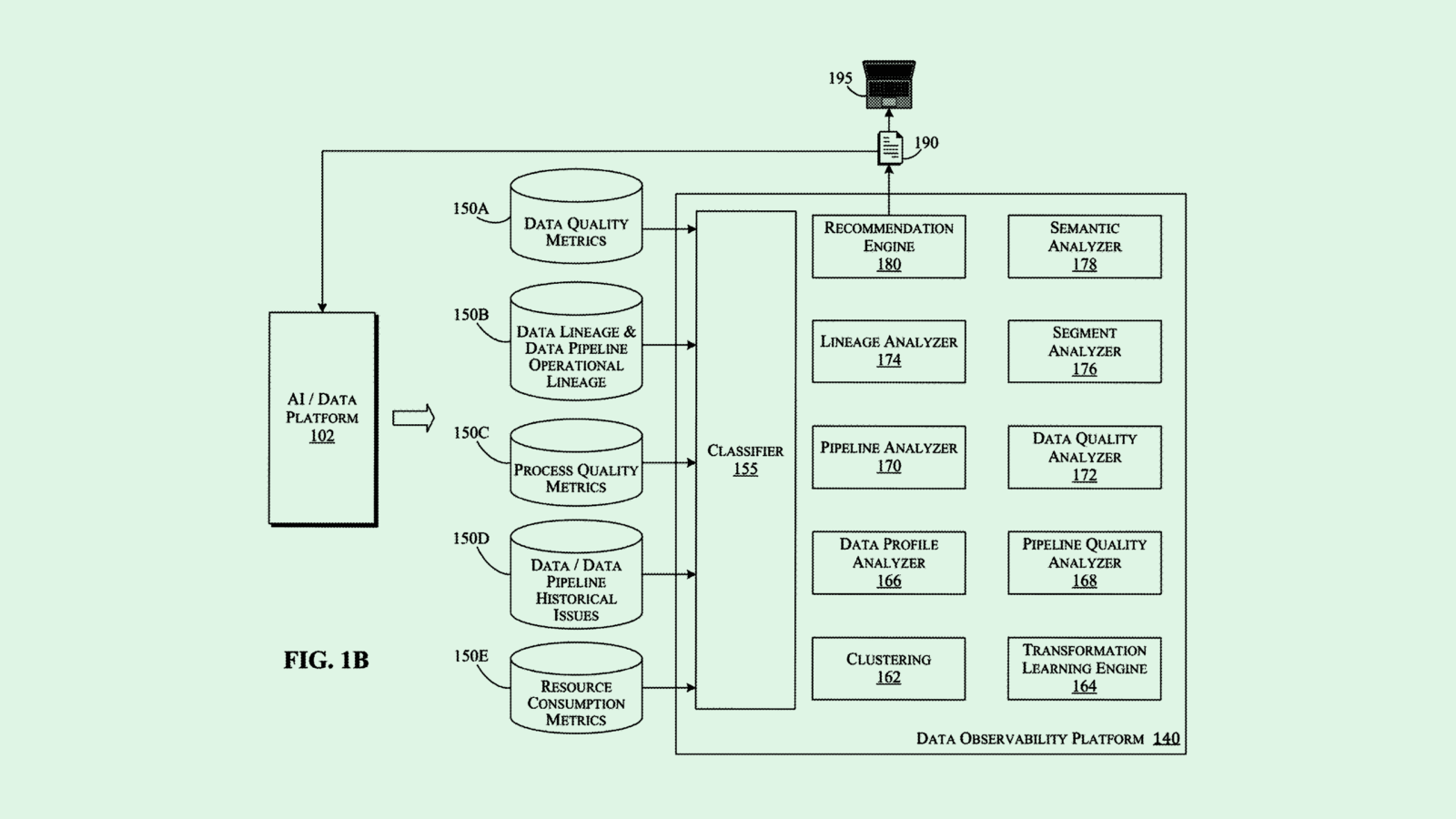
IBM may be looking for ways to sift out the best: The company filed a patent application for “modifying data pipeline(s) and dataset quality using data observability” that would monitor and improve the quality of data pipelines in real time.
The system continuously collects observability data from all data pipelines within a company’s architecture, checking criteria such as data quality and lineage, error history within the data pipelines, and resource consumption. Each of the datasets created from those pipelines is classified based on reliability of the data and usage, or how critical it is to operations.
Based on the classifications and observability metrics, the system then generates recommendations for how to improve the data pipelines or the quality of the data itself. This kind of real-time monitoring allows for preventative maintenance of data pipelines and creates more trustworthy datasets for a variety of use cases.
“Well-organized data pipelines provide the foundation for a range of data projects; this can include exploratory data analyses, data visualizations, and machine-learning tasks,” IBM said in the filing.
Data sits at the core of all AI models: The better the data, the better the model will work. And as enterprises navigate their AI strategies, whether they’re developing proprietary models or fine-tuning public ones, getting their hands on large amounts of high-quality data is imperative. Tools like IBM’s could streamline that process.
Patents like these add to a number from IBM and other tech firms that seek to offer peripheral technologies to support AI adoption and development. While IBM doesn’t sit among major model providers, developing and snagging IP for tools that help carry this tech transformation could prove to be lucrative as adoption marches on.
Extra Upside
- Let the Chips Fall: Nvidia is in talks with the U.S. government about shipping more advanced chips to China.
- I’m Drivin’ Here: Waymo received permission to test its autonomous vehicles in New York City.
- International Expansion: OpenAI announced plans to open an office in New Delhi, its first office in India.
CIO Upside is a publication of The Daily Upside. For any questions or comments, feel free to contact us at team@cio.thedailyupside.com.
