Booz Allen Patent Could Weed Out Security Leaks Early
Bad actors are finding vulnerabilities faster than ever. Preventative testing might be able to mitigate attacks.
Sign up to get cutting-edge insights and deep dives into innovation and technology trends impacting CIOs and IT leaders.
Cyberattacks are getting more sophisticated. How can enterprises best stop a constantly evolving threat?
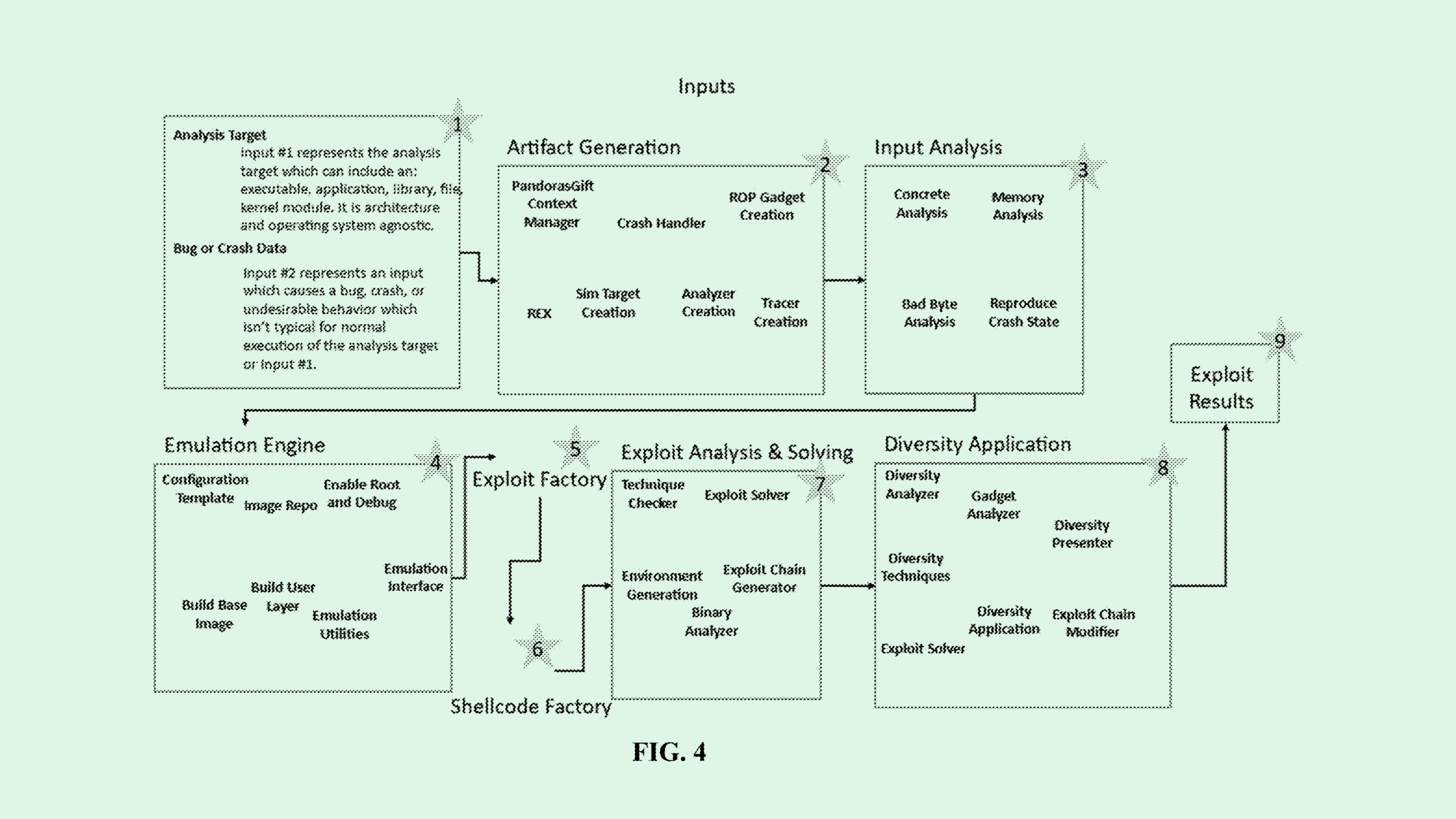
Tons of tech firms have sought patents for ways to detect and stop cyber threats in real time. But Booz Allen Hamilton is looking at ways to anticipate them: The company has applied for a patent for an “automated exploitation generation” system.
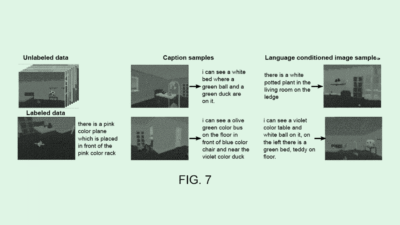
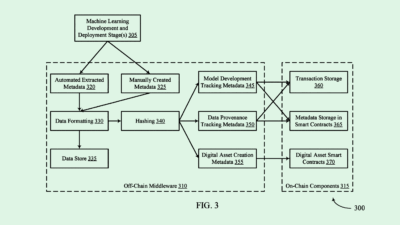
Booz Allen’s tech basically aims to detect and weed out potential vulnerabilities in software. This system would do so by creating a simulated environment to test any holes it’s identified without impacting real-world systems. Within this environment, the system runs a number of security tests, finding data security leaks or points where unauthorized action could be taken, and creates a report detailing the success rate and impact of the vulnerability.
This can help avoid attacks in a landscape “where the evolution of cyber-attacks is fast-paced and the effects of a cyber-attack can quickly cause widespread damage,” Booz Allen said.
AI has rapidly accelerated the sophistication of cyberattacks, with bad actors using it to quickly analyze code and find vulnerabilities. Plus, as AI is used within enterprises to build and deploy more code at a faster rate, bugs can easily slip through the cracks, said James Cassata, cloud security architect at Myriad360.
“Although it’s great that we can truly expedite the speed at which software is written, these solutions don’t necessarily think contextually about the other elements that go into the software, which could, of course, introduce vulnerabilities,” said Cassata.
And as bad actors get smarter, taking on their attacks as they happen may not be enough. Anticipating where these threats may strike could be the next step, said Michel Chamberland, founder of IntegSec. “If we don’t do it, the bad guys might already be there to find the vulnerability more easily and faster,” said Chamberland.
But while this tech can offer an additional layer, no single protocol is a panacea for security problems, said Chamberland. Security strategies require several layers, including training people to know what to watch for and constantly monitor for bugs and vulnerabilities, he said.
“You have to have many different layers of security … there’s no one thing that you can do to be prepared,” he said.