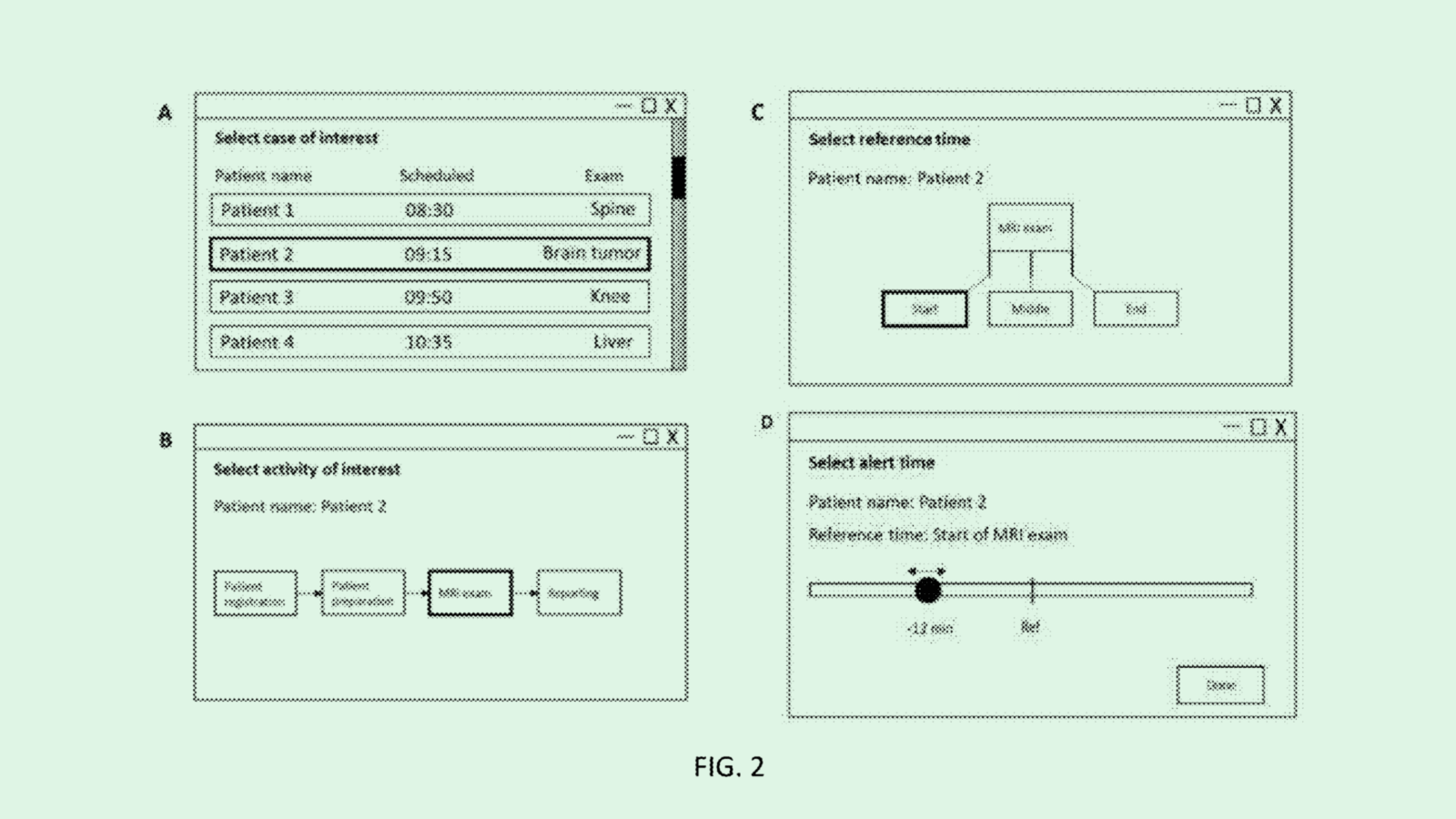
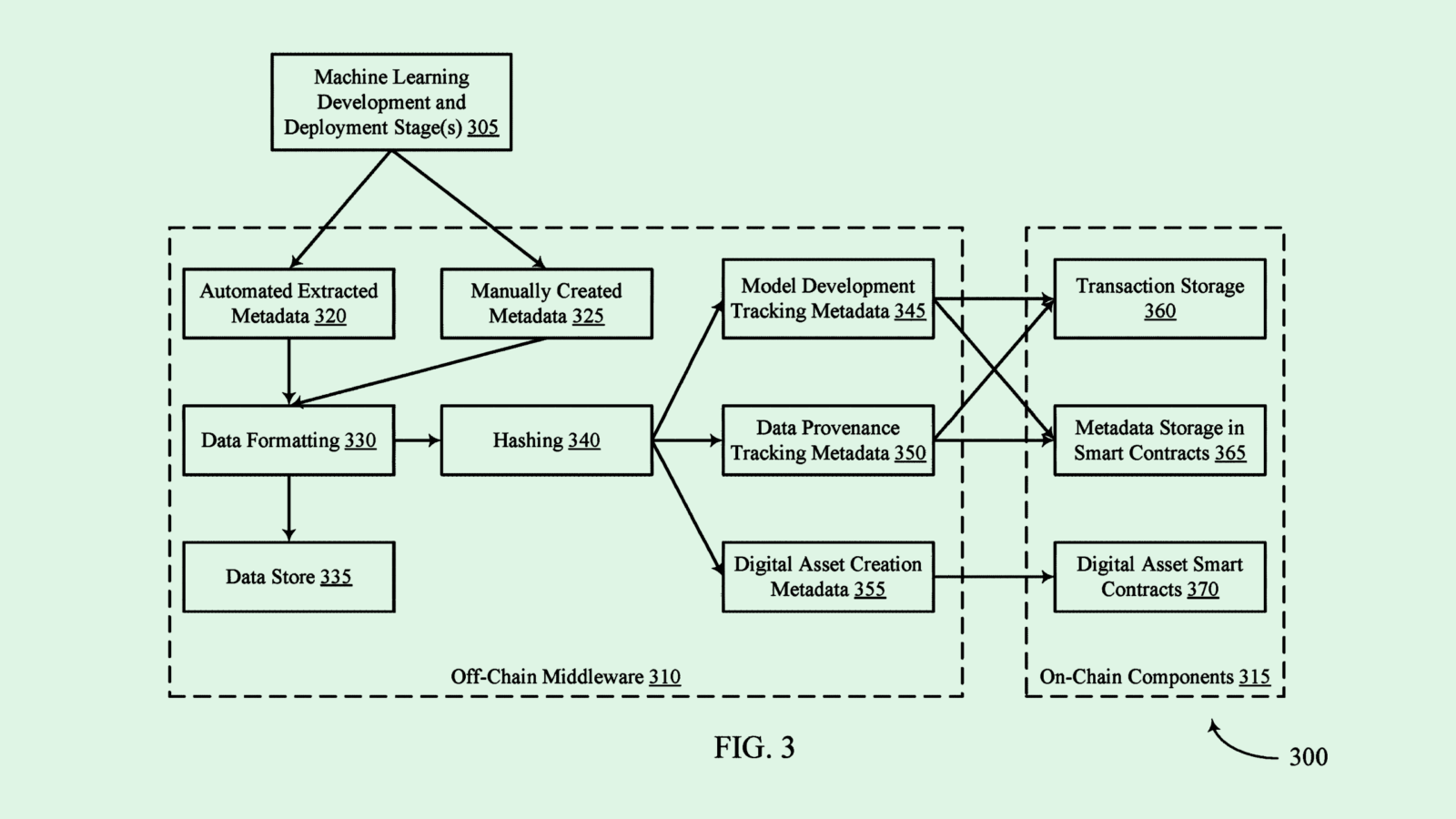
The Less You Know, the Better: Tech Moves Toward Data Minimization
‘At the end of the day, wherever that data is, it has to be protected’
Sign up to get cutting-edge insights and deep dives into innovation and technology trends impacting CIOs and IT leaders.
For a long time, the ethos of the tech industry was the more data, the better. Now some are beginning to realize that less is more.
Recent patents from IBM and Intel both highlight an increased focus on data minimization, or the concept that the collection, storage, and utilization of user data should be kept to a bare minimum.
- IBM is seeking to patent a system for the “efficient deletion of data in dispersed storage systems,” or data that’s been stored across multiple cloud locations. This tech basically aims to get rid of out-of-date and unneeded data, which is helpful for data security, cutting costs, and improving performance of cloud environments.
- Intel, meanwhile, is seeking to patent a system for “verification of data erasure,” which verifies that “programmable circuits,” or hardware that’s customized to perform specific tasks, have been securely erased using digital signatures and private keys. This is important for maintaining the data security of hardware that’s commonly used in things like AI training.
We’ve seen patents with a similar goal of data minimization in the past, such as Google’s filing for anonymizing large-scale datasets and Twilio’s patent for personal information redaction. And it makes sense that these companies are tackling data minimization in their security practices: the more data your enterprise has, the more your enterprise needs to protect, said Clyde Williamson, senior product security architect at Protegrity.
“To have the data in the fewest places possible is really necessary, because security isn’t an infinite thing that we can just constantly add more of,” said Williamson. “And at the end of the day, wherever that data is, it has to be protected, it has to be monitored, we have to be able to audit it.”
But the drive to develop and grow data-hungry AI models is making it increasingly difficult for tech companies to reconcile their data-minimization needs, said Williamson. Not only do these models often come with their own data security vulnerabilities, but they also add to what security protocols need to cover.
Plus, data security slip-ups aren’t always the fault of the company that collected the data in the first place, Williamson noted, but rather the third-party companies and vendors that have access to that data by extension. A company’s data-security strategy is only as strong as that of its weakest vendor. “That is where we see a lot of the vulnerabilities and compromises that we see in the news right now,” he said.