Microsoft Patent Tracks Down Software Vulnerabilities, Cyberattacks
In the face of a wide-spread outage, such as what occurred with Crowdstrike last Friday, there’s only so much the company can do, one expert said.
Sign up to uncover the latest in emerging technology.
Microsoft wants to keep its eyes peeled.
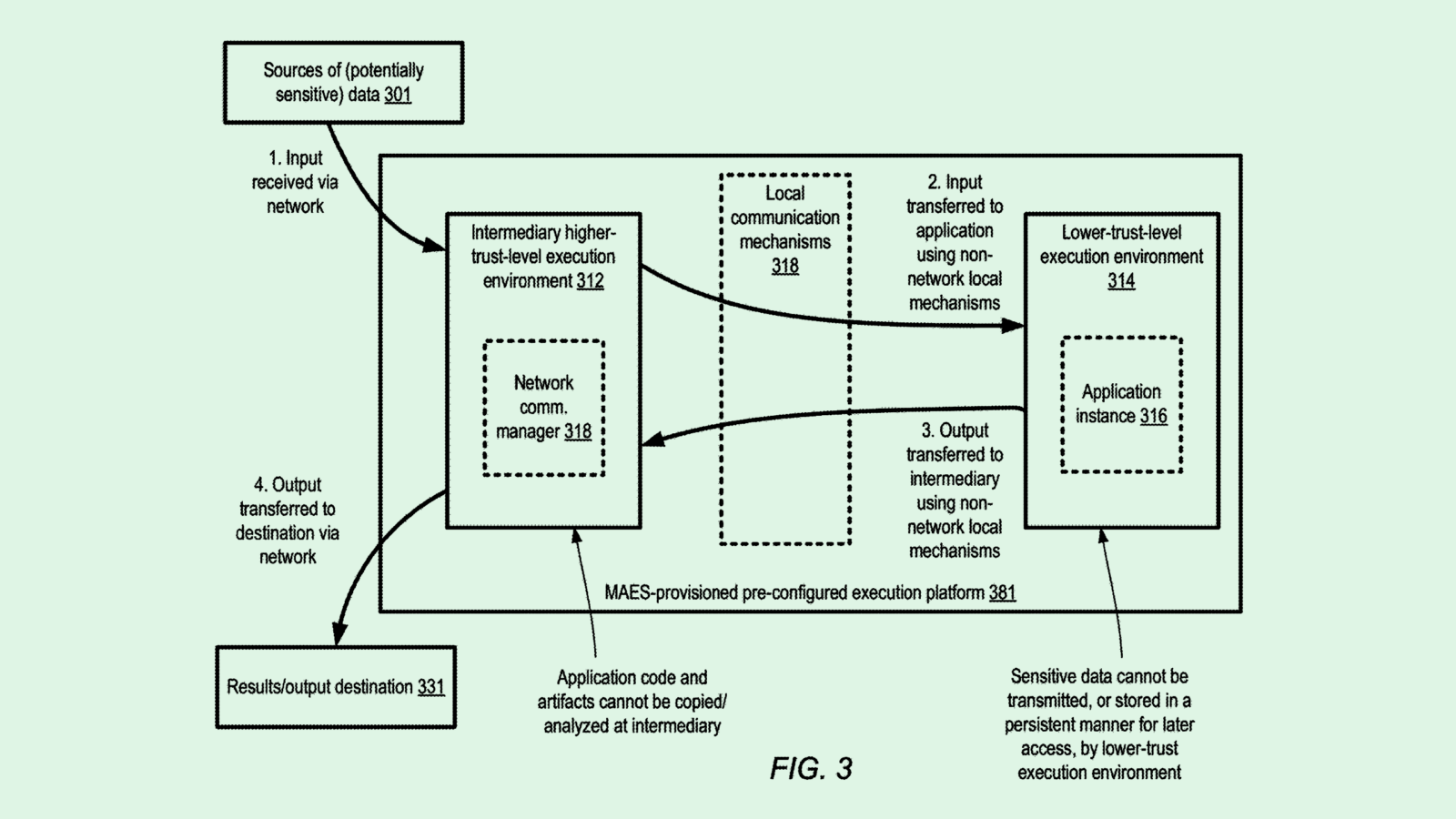
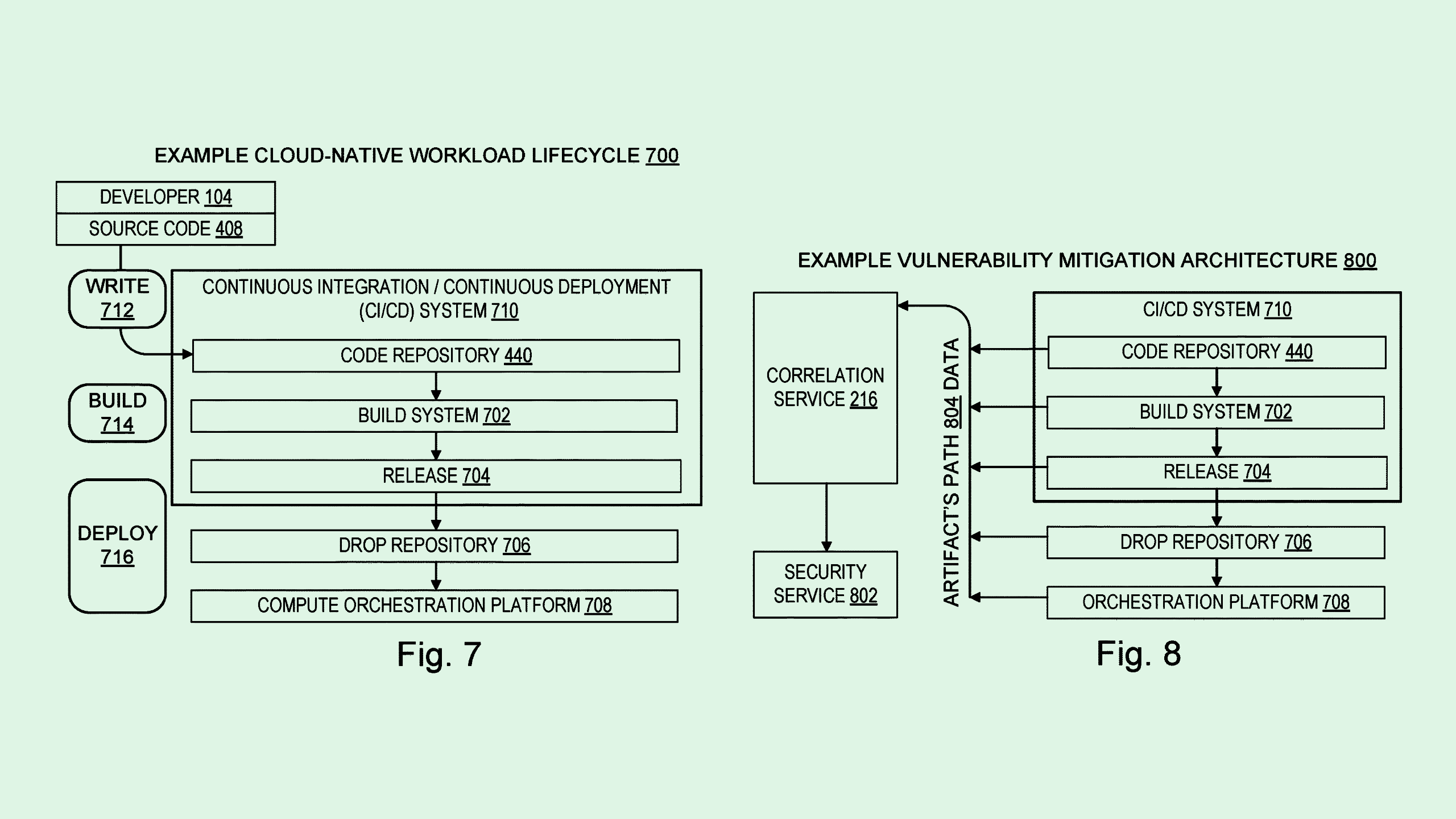
The tech firm is seeking to patent “security vulnerability lifecycle scope identification,” aiming to find faults in source code through different stages of development and deployment. The goal is to identify “the scope of performance flaws and security vulnerabilities” and avoid trying solutions that are “unnecessarily inefficient or incomplete.”
“No single security mechanism is able to detect every kind of cyberattack,” Microsoft said in the filing. “But sometimes combining and layering a sufficient number and variety of defenses and investigative tools will prevent an attack, deter an attacker, or at least help limit the scope of harm.”
Microsoft’s tech tracks these vulnerabilities through a collection of “software artifacts,” which can include anything from source code files to documentation to metadata that’s created in the process of software being developed. This system tracks the “artifact identifiers” of each of these pieces to find the paths that connect between them, essentially creating a digital trail to find where pitfalls may have occurred in the software development lifecycle.
If a pitfall is found, the system may automatically “resolve ambiguities” related to it, such as finding which developer is responsible, discovering whether that particular software has been deployed, or identifying related vulnerabilities.
Microsoft’s patent is akin to a security framework called SLSA, or Supply Chain Levels for Software Artifacts, which essentially aims to help trace where software breakdowns originate. Though similar tech exists, it’s hardly surprising that Microsoft would seek to patent it, said Ashley Manraj, chief technology officer at Pvotal Technologies, as it’s common for tech in patent applications to skew as broad as possible.
Microsoft can keep its own side of the street clean with tech like this. But in the face of a widespread outage, such as what occurred with Crowdstrike last Friday, there’s only so much the company can do, said Manraj. Because Crowdstrike is a third-party software vendor, he said, Microsoft likely has little visibility into the ins and outs of its software development and deployment pipeline.
Friday’s outage stems from a Microsoft configuration that allows security vendors like Crowdstrike to operate at the kernel level, giving them the highest level of access possible to an operating system’s resources. “If you get a crash, it crashes the machine completely,” said Manraj. “There’s no level of OS to protect you. Mistakes lead to the device crashing.”
Microsoft attempted to restrict this in 2006, but received pushback from security vendors and EU regulators. Now, the company may once again be calling to restrict vendors’ access to Windows’ kernel level, noting in a blog post last Thursday that the company must prioritize “end-to-end resilience.” Given the scale of the incident, Manraj said, the odds may be in their favor.
The crash may also lead to a change in the software market entirely, said Manraj, encouraging tech firms to utilize a broader diversity of vendors, rather than relying on one. That way, rather than 8.5 million devices going down, an outage may not be as severe, he said.
“I think that’s a lesson for the really big enterprises: Source with multiple vendors, and run different software stacks,” said Manraj. “Diversity is not always an enemy.”