Intel Adds a Layer of Protection to Edge Computing
Intel wants to protect everything from you smartphone to your HVAC.

Sign up to uncover the latest in emerging technology.
Intel wants to keep its client data locked down no matter where it’s located.
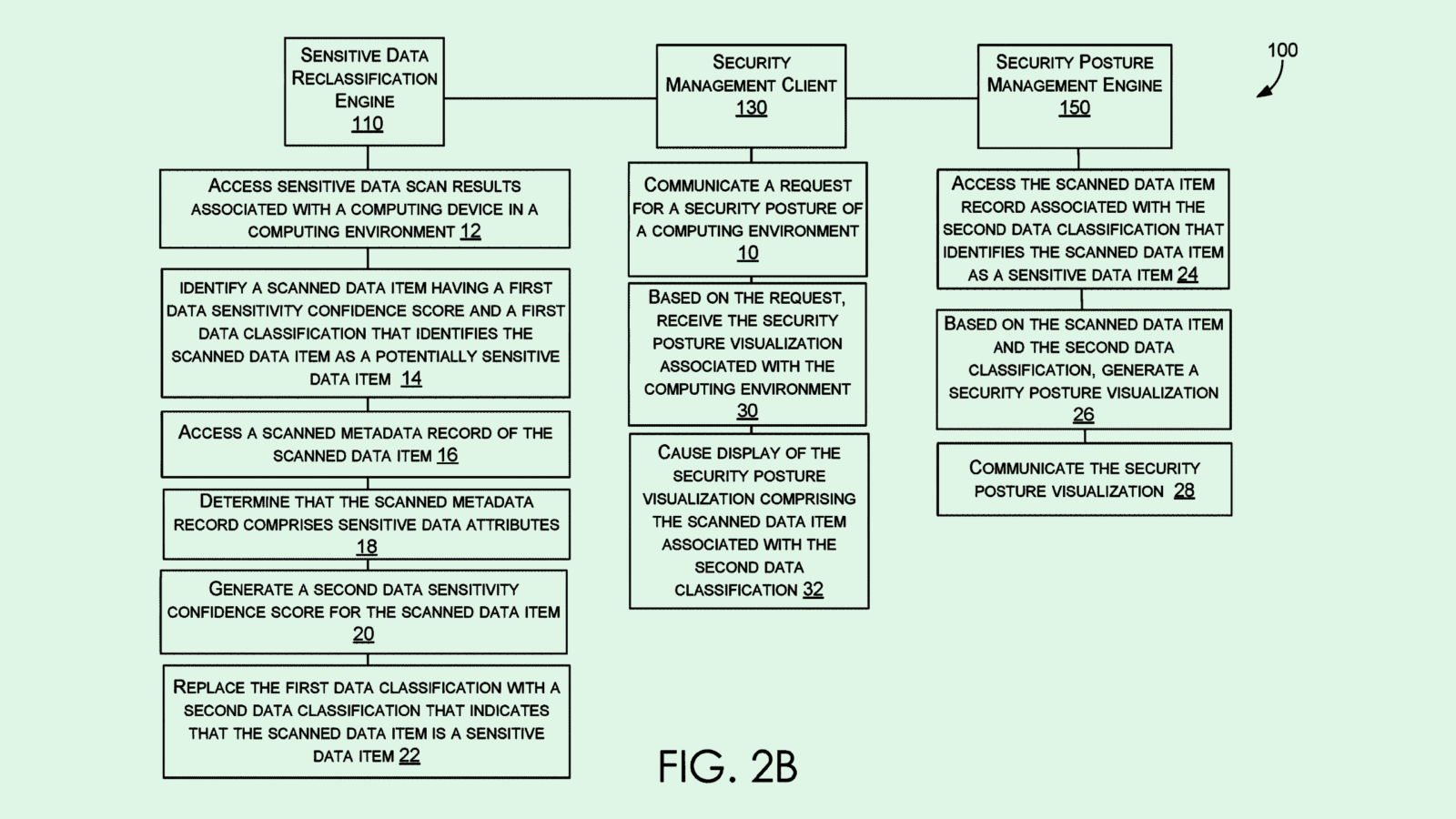
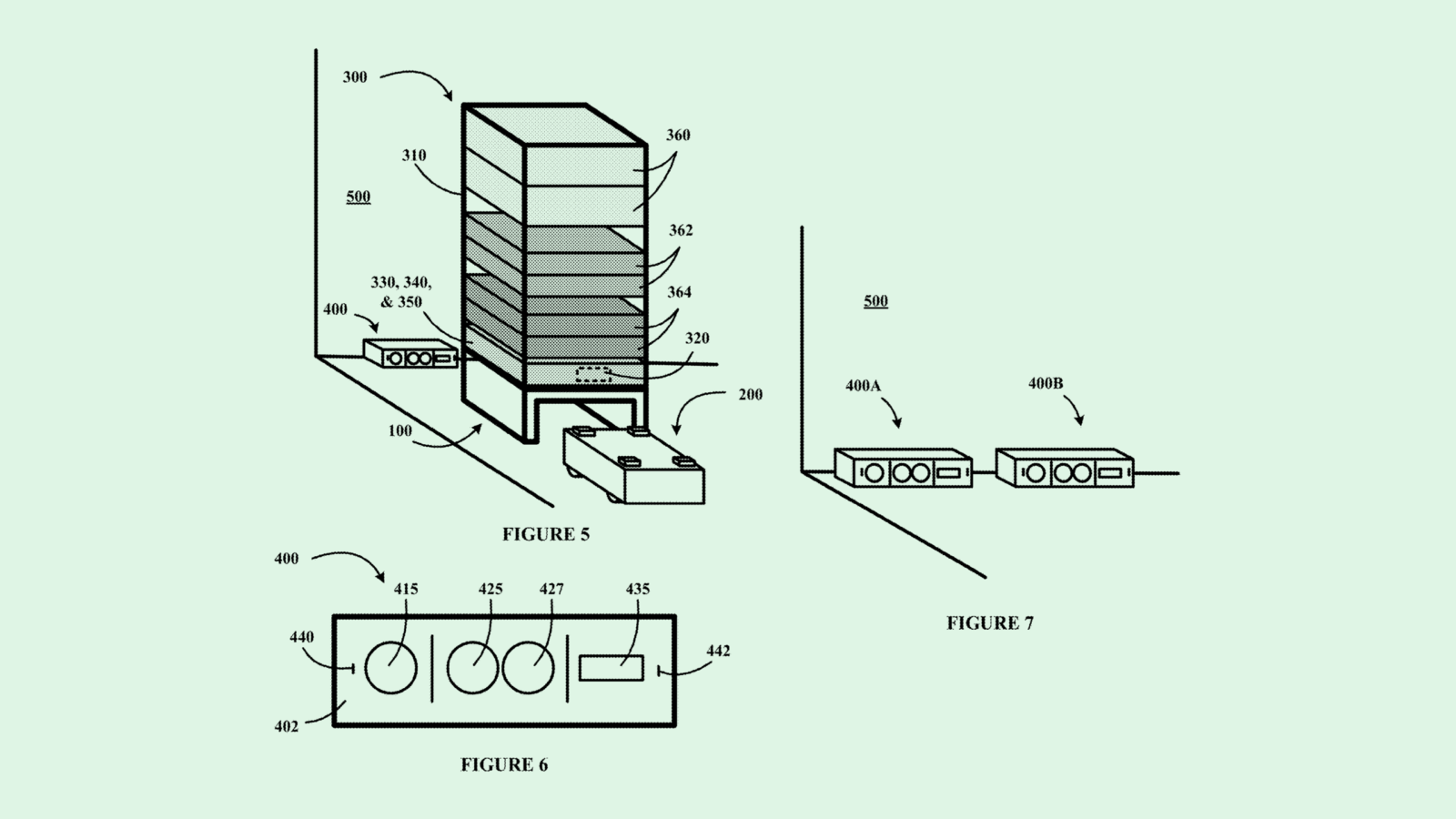
The company filed a patent application for multi-tenant data protection in “edge computing environments.” The system will allow tenants (i.e. mobile devices, smart TVs and speakers or even autonomous vehicles all connected in an Internet of Things ecosystem) to share data securely among one another without risking vulnerability, because it essentially gatekeeps which devices are allowed what data and memory.
Different clients are assigned to different “shared memory regions” within an edge computing environment, or basically different pots of memory storage for a number of different devices in a network. For each region, the system tracks “workloads” among these tenants, or what tasks each device is trying to accomplish, to find out which devices need access to what data or memory.
This system protects said data using “memory access requests,” which checks that the tenant requesting access has a specific reason to do so. This, in turn, allows for “collaborative execution of data flows and chain of services” among one another, Intel said.
Imagine it like school: A principal would give specific keys to different teachers based on the class they’re teaching. An art teacher may have the key to an art supplies closet, while the band teacher has the key to the instruments closet. If anyone needs something from their closets, they’d need a valid reason to access it.

Within edge computing environments, data is processed at the source that the data is collected, whether that be a smartwatch, a vehicle, a vending machine or anything else that falls under the umbrella of the Internet of Things. Because those kinds of devices can be so wide-ranging, there are tons of possible entry points for a talented hacker, Ari Weil, VP of marketing at data security firm Cyera.
In one infamous example, Weil noted, hackers compromised the systems of retailer Target by hacking into an internet-connected HVAC system in 2013. In another, a hacker gained control of someone’s Jeep while they were driving it in 2015. Since then, connected devices have only become more ingrained in our day-to-day lives.
“Isolation (between IoT devices) needs to be there to make sure that the things a hacker can access wouldn’t be things that are destructive to the functionality of something, a safety concern or potentially something that would leak IP,” said Weil.
Companies like Intel, Google, and Qualcomm that work on edge technology want to build security “as close to the device as possible,” said Weil. “And you can’t get any closer than the chip.” By weaving this kind of security into its chips, he said, Intel could effectively dominate relationships with equipment manufacturers by providing a layer of defense alongside the ability to “control, configure and manage all through one provider.”
The more tech in this vein that Intel offers, the more it could consolidate deals by packaging offerings together, allowing its partners to slim down their networks of supply chain providers (and giving Intel a stronger grip on the market). Though other companies are plugging away at edge computing tech, “the competition piece will come down to people who … have the relationships to actually achieve the sort of penetration that Intel can,” he said.