Raytheon Adds AI to Cybersecurity Defense Lineup
Raytheon wants AI to create its playbooks for responding to cybersecurity attacks. It could help keep up with sophisticated threats.

Sign up to uncover the latest in emerging technology.
Raytheon wants AI to do its emergency prep.
The aerospace and defense contractor filed a patent application for a system for “automated generation of playbooks for responding to cyberattacks.” Essentially, Raytheon’s gives users recommendations on what actions to take in the event of a cyber attack. This patent seems to specifically counter malware attacks as they can vary widely, therefore defense and protection strategies need to be varied, too.
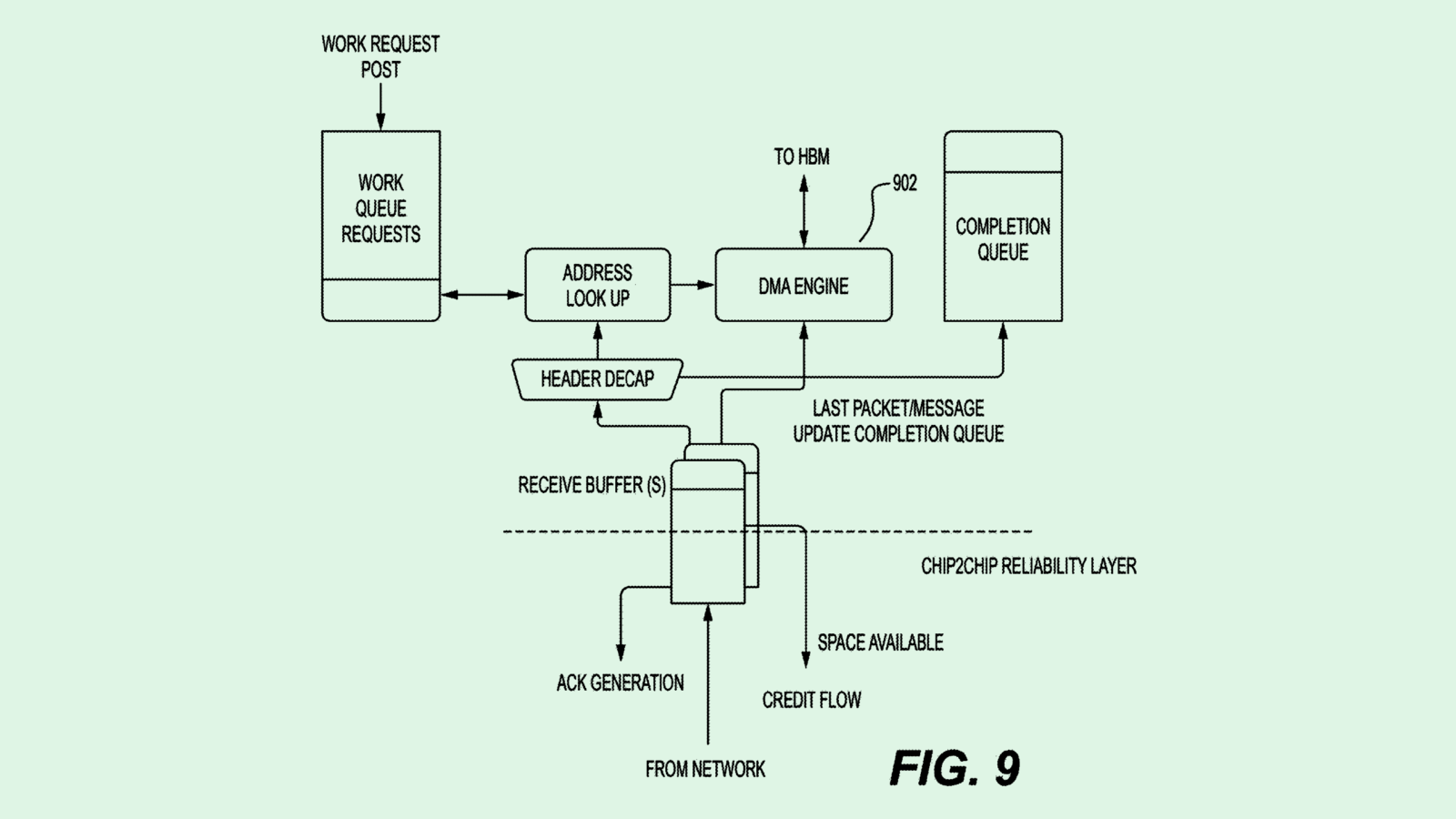
Here’s how it works: This system operates using a database containing information on several different types of cybersecurity events, as well as their corresponding response actions. When the system receives notice that a cybersecurity event is happening, it will generate an “event response playbook” detailing what needs to be done to defend against it. If more than one event happens, then the playbook will be tailored to respond to multiple events.
Raytheon noted that this system could rely on a number of different types of AI, including machine learning, deep learning and neural networks to “dynamically and optimally generate new or enhance playbooks.” In that respect, this system would continuously learn and evolve its playbooks both as cyberattacks and response tactics get more complex.
The defense firm noted that existing playbook systems are complex and tedious to deploy, and that human-developed playbooks “can compromise playbook reliability due to human error during development or implementation.”

Given that Raytheon’s entire business is defense contracting, keeping things locked up tight is likely of high priority. Both the Department of Defense and its supply chain are far more prone to cybersecurity threats than the average business, and have far more to lose if something falls through the cracks, said Ali Allage, CEO of BlueSteel Cybersecurity. Plus, Allage noted, defense department vendors themselves have strict legal requirements in safeguarding information.
“It’s not a creative space,” said Allage. “You can’t test things and be imaginative about it. It’s more like ‘This thing better work, and it better work the first time around.’”
Outside of defense contexts, a system like this could be useful for any government entity that holds a lot of sensitive and confidential data, whether it be the IRS, Census data or intelligence agencies.
However, the lack of interoperability between systems may cause some issues in implementation, said Allage. Theoretically, a system like this would need to monitor activity from disparate sources to formulate any sort of countermeasure. But because government entities and their vendors often have firewalls around every part of their organizations, working around that wouldn’t be easy.
“Everything has its own containers, everything has its own permissions, everything has its own classifications,” said Allage. “You have to be very cognizant of that, because it comes with a lot of red tape.”
This may also help fight against the classic adage that putting up a 10-foot wall invites bad actors to build a 12-foot ladder. Since this system depends on AI to be constantly watching and learning, this has the capability to evolve as the attackers’ strategies get more aggressive. However, Allage noted, it won’t completely eliminate the problem. “You’re always gonna have a continuous attack. It’s just about who’s algorithms are smarter than the others.”